Thursday, October 01, 2015
Exclusive: China will not soon break 100 PFlops supercomputing limit
Wuxi Supercomputer center's 17MW of power is enough for LINPACK ~90 PFlops. But, in 2017 it will upgrade to 28MW of power. That should be enough for 165 PFlops. However, with its new own accelerator say only 50% faster than the 2,4 TFlops current one, its supercomputer star could hit 240 PFlops in 2018 !! US imposed sanctions ? What sanctions ??
___________________________
99% BAD HARDWARE WEEK:
Monday, August 24, 2015
After MH370 case we have identical disappearance Intel's BRW EP/EX
The heterogeneous memory management (hmm) patchset implement a new api that
sit on top of the mmu notifier api. It provides a simple api to device driver
to mirror a process address space without having to lock or take reference on
page and block them from being reclam or migrated. Any changes on a process
address space is mirrored to the device page table by the hmm code. To achieve
this not only we need each driver to implement a set of callback functions but
hmm also interface itself in many key location of the mm code and fs code.
Moreover hmm allow to migrate range of memory to the device remote memory to
take advantages of its lower latency and higher bandwidth.
Some of our internal sources told us that the Enterprise declination of Broadwell architecture is recently disappeared from the latest Intel roadmaps. The Enterprise CPUs will go directly from Haswell to Skylake. ??
___________________________
99% BAD HARDWARE WEEK: At IDF 2015 Intel CEO hinted Broadwell EP/EX will use XPoint DRAM4. Well, that seems quite justified reason for its roadmap disappearance on Lunedì, 13 Luglio 2015 10:01.
Some of our internal sources told us that the Enterprise declination of Broadwell architecture is recently disappeared from the latest Intel roadmaps. The Enterprise CPUs will go directly from Haswell to Skylake. ??
___________________________
99% BAD HARDWARE WEEK: At IDF 2015 Intel CEO hinted Broadwell EP/EX will use XPoint DRAM4. Well, that seems quite justified reason for its roadmap disappearance on Lunedì, 13 Luglio 2015 10:01.
Sunday, August 23, 2015
If math and physics don't lie MH 370 is here
___________________________
99% BAD HARDWARE WEEK: 4819 km east from Diego Garcia island, just under the Inmar satelite. And 1000 km east from the last MH370 contact place. But wait, what about Maleysian radar seeings? They lied. What about Reunion MH370 flaperon ? Fake evidence. “If this had been the case with the MH370, one would expect much smaller debris than a flaperon,” said the expert. According to a Toulouse aeronautics expert who requested anonymity, the element of the wing would not have floated for several months at the water’s surface but would have drifted underwater a few meters deep.
Who responded to Vietnam flight control call ? Another plane that later landed on maleysian airport at pic above. But remember, both can't be right: Maleysian authorities and Inmarsat. Then chose your version yourself. Or check this airplane parking at South Kalimantan at distance 4819 km from Inmarsat projection. To get there you have distinct Doppler shift only south flying airplane get. Malayasian radar findings was nice distraction in just opposite direction.
Friday, August 21, 2015
Update on Intel's Xpoint: HDD is dead in 10 years !
Thin film PCMS as the initial option has one drawback Intel kept well hidden at announcement. It has SET time 10 times slower than DRAM. That means device writing is stil 100 times faster than NAND's.
Yes, might be byte addressable and fast enough for NVDIMM
However, it is correct Intel's claim that PCMS is 1000 times more durable than NAND. Well ,100 times faster but not at least 100 times more durable should mean 100 times SHORTER writing device life span !Yes there is option for opening new blocks for writing, but inevitable complexity is with allocation table rewriting etc and overall realibility.
In Xpoint G1 2016 we will get only 5 times better performance than NAND SSD. In G2 2016 are possible 25 better times, provided there is available so fast NVM interface!! See pic below.
___________________________
 99% BAD HARDWARE WEEK: NVDIMM version 500 times faster than NAND (that Micron named EM G1) is predicted for year 2017 with Purley Xeon ( see the previous post). Anyway, since 2006 HDD has been only arhive device, as Jim Gray from Microsoft noticed. After that year we have seen enterprise flash SSD reaching mainstream maturity. That is why China just before Xpoint announcement offered hefty $23 Billion for Micron and its production facilities.
99% BAD HARDWARE WEEK: NVDIMM version 500 times faster than NAND (that Micron named EM G1) is predicted for year 2017 with Purley Xeon ( see the previous post). Anyway, since 2006 HDD has been only arhive device, as Jim Gray from Microsoft noticed. After that year we have seen enterprise flash SSD reaching mainstream maturity. That is why China just before Xpoint announcement offered hefty $23 Billion for Micron and its production facilities. Tuesday, August 18, 2015
Intel's Optane drive bested its top NAND based SSD 5X !
___________________________
99% BAD HARDWARE WEEK: OK. After recent 1000X XPoint announcement we got more realistic 5X demo at queue depth of 8 ! And max 7X more performance at queue depth 1 ! We can clearly see from pic above that max peformance improvement at time of drive production is 10X, and with average queue depth 8 mere 7X ! And what about announced 1000X improvement? Well, in time with technology scaling. I am only joking. Partner Micron promised in 2017 faster EM gen 1. Is it Xpoint too ? Who knows?. Well, lets try find out. Intel will initially offer slower PCM based NVM, that is exposed on pictures above. Is it Xpoint ? Hardly, being too expensive to be competitive with 3D NAND. However, if Intel's marketing 3D calls Xpoint it is quite another matter :)) Intel hint on bulk storage make this breaktrough actually years known technology that Micron quit a few years ago. Or if the hint is fake, next to Bulk Transition solution, Tunnel Barrier. Filamentary ReRAM is anyway excluded.
HINT on Tunnel Barrier use is the sole name of technology: OPTANE !
However Purley server 2017 leak shows us support for Adams Pass memory interface 500X faster NVM. Well, that might be only XPoint and nothing else. There are two NVM technologies, for 2016 and 2017. 2016 one will compete with NAND, the 2017 one with volume DRAM4. Briefly, byte addressable Xpoint 2017 will be 100 times faster than NVM delivered next year in two successions.
Batman killed in action !
Broken Batmobil to blame.
___________________________
99% BAD HARDWARE WEEK: Alelujah ! Though it was Batmobil classic, not a self driving one ! After Superman broke his spine riding a horse it is obviosly safer for heros to fly.
Sunday, August 09, 2015
Definitely, no both scenarios for MH 370 !
Update: according to aviation sources, MH370's climb to 45,000 feet (well above its designed ceiling) would have probably required reducing weight by dumping fuel. This calls the accuracy of this altitude data into question.
___________________________
99% BAD HARDWARE WEEK: At 15 km altitude, with on board fuel for no less than 4400 km flight ?? NO ! It is however possible with previous fuel dumping, but there was no Mayday call ! Instead, good night to flight control from captain !! Then somebody lied on tehnical data, and it is really monstrous !.
Beside, satellite who caputered alleged later pings is directly above Diego Garcia naval base. They must be direct sat link connected !! Hail could brake airplane window that urged pilot to turn flight back to protect his CABIN ! RApid decompression should force him for steep down maneuvre and no respond to controll calls. Hail could disable ACAR and transporders too ! Anyway, the pilot had enough time to enable autopilot.
Friday, August 07, 2015
OTH radar at Diego Garcia able to detect small airplane at 3000 km distance
Well, if it is installed at all. Here is what IS INSTALLED AT DIEGO GARCIA:
The GEODSS system can track objects as small as a basketball more than 20,000 miles away and is a vital part of the AFSPC's space surveillance network. Please note it is plascd South of Equator in the West prevailing ocean currents ! Countervise to those North of Equator.
___________________________
99% BAD HARDWARE WEEK: Somalija, MAdagascar, Reunion, JEmen, Mumbai in India, Indonesia western part, Cocos Island that belongs to Australia are in OTH RANGE. OTH means Over The Horizon.
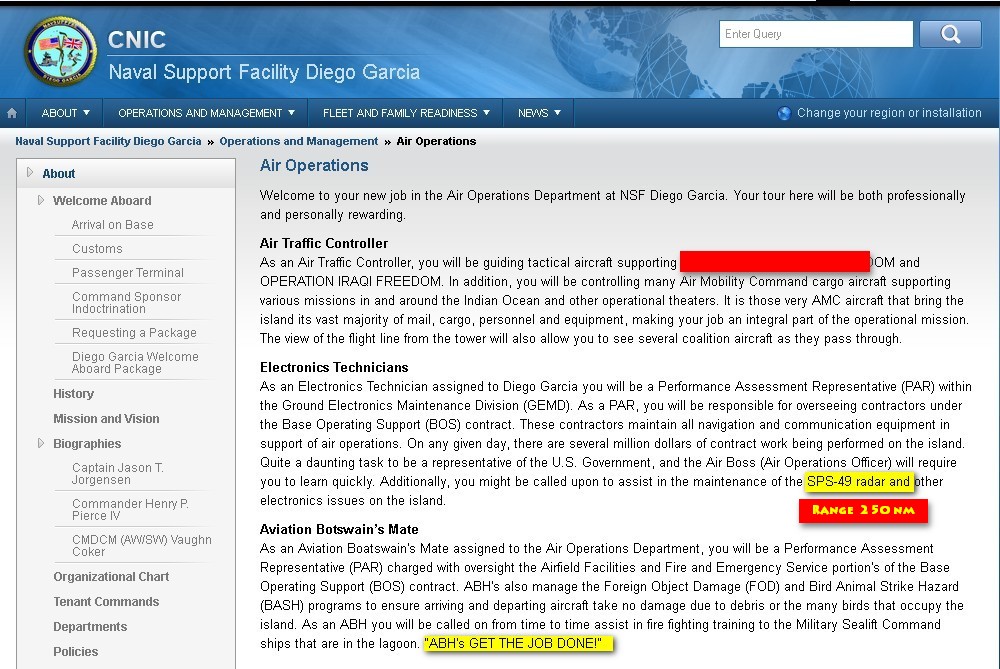
SCHOCKA: No one could unrecognised get closer to Diego Garcia than 400 km !. Because of SPS 49 air radar (inside red range circle in a distance map above).
Is Apple new Atlantis ?
Lost $50B in a single day !!
___________________________
99% BAD HARDWARE WEEK: However, profits still better than Google's !
___________________________
99% BAD HARDWARE WEEK: However, profits still better than Google's !
Who censored MH370 flight from flightradar24 site ?
___________________________
99% BAD HARDWARE WEEK: Must be someone extremely powerfull. Like in Wikileaks case, flightradar is registered in Sweden ! By the way, below is what has been censored.
The current models said debris had likely been carried to the north towards the coast of Sumatra from the area off the west coast of Australia where the plane likely came down. However, place where it went down probably encircled on the pic above, is BELOW the equator, AND in the prevailing ocean currents towards island Reunion. Just in opposite direction.